There are several simple steps you can take to make your ILR-owned computer safer. While some of these guidelines are universal, some instructions are for computers owned by ILR only. If you are specifically looking for security tips for your personally-owned computer, please see Home Computer Management.
First, and most importantly, use complex passwords. Doing so will significantly help guard against unauthorized access to your computer and the data contained within it.
All ILR-owned computers are set up to automatically lock after a certain period of inactivity (usually 15 minutes); however, you can increase the security of your computer by manually locking your computer before walking away. To do so, just press Ctrl-Alt-Del on your keyboard at the same time; then, click on Lock Computer. When you return, just repeat the same keystroke (Ctrl-Alt-Del) and enter your password.
Reboot your system on a regular basis (preferably daily but no less than once per week) so that security patches will be properly applied to your system. This applies primarily to on-campus users or users who regularly connect to our servers.
Have you received an email from a bank or other institution you think may be spam but want to verify? DO NOT click any of the links within the email! Instead, just place your cursor over any link within the email, and look at the bottom left-hand corner of the main Eudora or Thunderbird window. There you will find the actual address to which you would be taken if you were to click on the link. If it doesn’t match what’s displayed within the body of the email, it’s likely a hoax. If the addresses do match, it’s still best not to click on the link. Instead, open up a web browser and type in the address of the website in question.
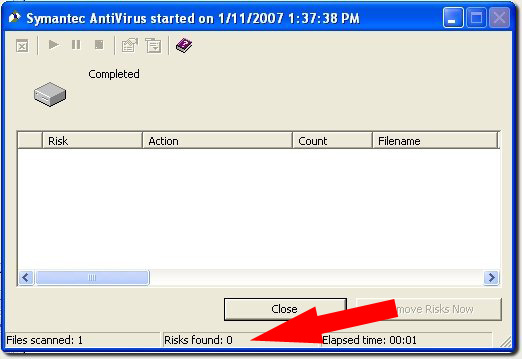
If you receive an email with an attachment you weren't expecting, even if the sender is someone familiar to you, a possibility that the attachment is malicious exists. The best way to determine whether or not an attachment is legitimate is to email the sender to ask about the legitimacy of the attachment. Alternatively, you can save the attachment to your computer and then run a virus scan before opening the file. After saving the attachment, just right click the file and select Scan for Viruses. A Symantec AntiVirus window will appear, and once the scan is completed, verify that the risks found is zero. If it isn't, DO NOT open the file; delete it. Then, contact the sender to alert them to the issue with the file.
As a matter of course, CIT will disable network access to on-campus systems that display signs of system compromises or that visit websites known to have been compromised. Network access will not be restored until ILRTS can clean or rebuild the system.
